
TL; DR: Mobile devices have become the primary target for cybercriminals. And their attacks have evolved to new heights of sophistication. Now, mobile use on personal devices not only affects the user but can also impact their employers. Traced helps businesses protect company data across employee devices with its privacy-first mobile threat defense application. We spoke with Benedict Jones, CEO of Traced, about how the platform detects threats using AI, protects employee privacy, and safeguards companies against harmful attacks while staying simple to use.
Mobile internet use has exploded. Since 2015, mobile internet traffic has risen by a whopping 75%. Gone are the days when phones were solely used for communication. Not only has our relationship with mobile phones evolved, so has the threat landscape, raising the question of the security of our little digital lifelines.
In the past, bad actors would mainly unleash attacks on email or desktop computers and avoid exploiting mobile devices because of the unfamiliar technology. But this disparity gap has since closed, and cybercriminals have more attack surface than ever with mobile devices. Now, it’s not difficult to come by an annoying phishing SMS asking for your credentials or for you to click on suspicious links.
These mobile threats can even affect businesses. Twilio, an industry-leading customer engagement software company, had two employee accounts compromised by a social engineering scheme in 2022. A bad actor posing as an IT team member or system had sent these employees a text message suggesting their passwords had expired, prompting them to log into a false URL.

“Cybercriminals will use that to walk in the front door, impersonate the user to steal confidential data, and then fundamentally have them held to a ransom. The exact cost of that data breach isn’t exactly known. But the implied loss of enterprise value is about $2 billion,” said Benedict Jones, CEO of Traced.
Traced helps companies protect themselves from mobile threats similar to those that attacked Twilio. Its mobile threat defense platform has a privacy-first design and establishes zero trust to ensure every step of the mobile journey is secure for companies and their employees. “Our vision as a company is to live in a world where anyone can comfortably, easily, and securely use the same mobile device for both work and play,” said Benedict.
What Traced Does Differently
Benedict has an extensive career in the cybersecurity space, working for security titans McAfee, Sophos, and Intel. While working for these companies, he learned a lot about threat research and identifying new techniques to manage risk. During his research, Benedict identified the three primary challenges businesses face in securing their operations against mobile attacks.
The first challenge is that many existing cybersecurity solutions are too complicated to use and deploy for teams. Secondly, many mobile threat defense solutions use outdated and ineffective technologies that are unable to detect novel mobile threats. Lastly, typical mobile threat defense apps are privacy-invasive and share too much information about employee mobile use.
“Compounding these three challenges led and inspired me to develop a better solution, one that solves these challenges,” said Benedict.
Traced sets itself apart by delivering a solution that is private enough for employees to feel comfortable on their mobile devices, easy enough to deploy for everyday teams, and secure enough to detect and protect users from the threats of today and tomorrow. It currently has more than 300,000 downloads and works with businesses from around the world.
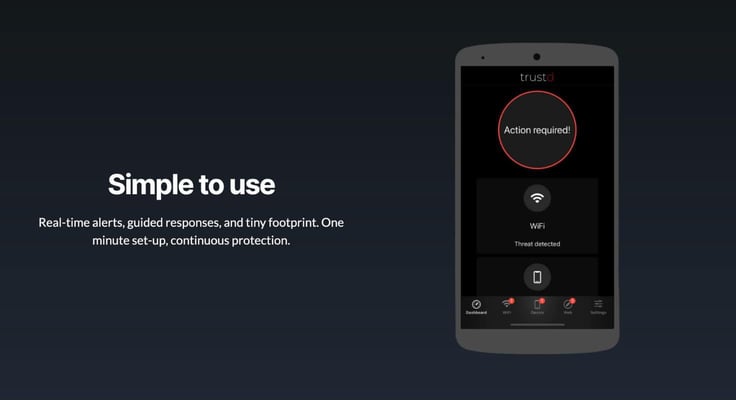
“One of the reasons customers choose us is not just because we can detect more quickly, by using things like artificial intelligence and so on, but also because we layer that in with security best practices,” said Benedict.
Traced uses a mechanism to automate the enforcement of zero-trust principles. The Traced platform assumes and acts as if a device is compromised until it can be proven otherwise. For instance, if an employee installs an app that isn’t trusted, Traced can automatically revoke that employee’s access to company data on their mobile device. This method also prioritizes privacy as it does not require scary permissions nor share private information with your company from your personal mobile.
“What we do for personal mobile devices is share red, amber, or green health statuses with the organization. This way, we can keep employees happy because companies won’t have visibility of what they’re doing, but companies are also happy because they’ve managed the risk,” said Benedict.
Top 2 Mobile Threats: Phishing and Malware Apps
The threat landscape has evolved over the decades. As mobile devices rise within the ranks for usage, threat actors have added them as their new stomping grounds to launch attacks against unsuspecting users. Benedict told us that phishing and malware apps are the two top mobile attack vectors.
“Sixty-three percent of successful mobile phishing attacks have taken place on iOS. There are a few reasons for this. They tend to be more lucrative targets and, therefore, more heavily targeted by cybercriminals,” said Benedict.
Benedict also said that while iOS users may be more vulnerable to phishing attacks, Android users are currently more commonly exposed to malware applications.
“You’re more likely to accidently install a malware app on Android than iOS as Android has an open ecosystem from which users can install their apps. This is however somewhat counteracted as Android permit anti-virus apps on the Google Playstore which enables independent cyber security experts to protect your device, without relying solely on native protection,” said Benedict.
While this accessibility can be beneficial, it also leaves users susceptible to apps that haven’t been validated security-wise. Apple intend to make the side-loading applications onto iPhones possible in iOS 17, which will increase the need for third party anti-virus apps on the platform.
Traced’s antivirus application, Trustd MTD, helps users safeguard their phones from malicious apps and phishing. “Trustd MTD uses artificial intelligence, layered in with static detection and real-time cross-industry cloud lookup for malicious apps, websites, and phishing attacks that target Android, iOS and iPadOS. So, Trustd MTD can block these threats as they are the most common mobile attack vectors” said Benedict.
Using AI to Detect Nuances in Threats
Artificial intelligence plays a significant role in Traced’s detection technologies. “We use artificial intelligence to spot differences and nuances between apps or websites to identify and differentiate whether an app or website is clean or malicious,” said Benedict.
These nuances can often be found in SMS phishing links because cybercriminals like to use structural patterns and social engineering to create them. They often use play on words and other combinations so their links can resemble those of an actual organization and fool users into logging into their attack.
“So we took a massive dataset of phishing links and clean links to train our AI model, specifically a deep learning model, to spot those differences,” said Benedict.
Its engine can also do the same for applications. Traced looks at permissions, language, and other features to indicate potential footholds of malicious apps. A valid example would be a calculator app asking for camera access. The AI would automatically detect that an app with that purpose would not need those permissions and mark it as malicious.
“That’s what AI does a better job of than static lists because it can make a decision on the fly. As mobile security researchers, we aren’t necessarily on every single device, but an AI model can be. And it can make that point-of-time gatekeeper decision if you’re coming in or not,” said Benedict.


