
The web hosting world has always been a prime target for privacy threats. Small business owners and hosting providers constantly seek new security and privacy features to protect against these attacks.
According to a recent HostingAdvice.com survey, 53% of respondents say their biggest concern when visiting a small business website is their personal information may get sold to a third party. Other top concerns include a website asking for too much personal information and lacking HTTPS encryption1.
More than ever, protecting your personal data online is becoming increasingly important. And as a business owner or web designer, you can miss out on potential customers by not offering the latest security and privacy features.
Let’s review some key privacy and security features you should always look for in a web hosting provider.
-
Navigate This Article:
Privacy Features for a Worry-Free Website
Your web host’s privacy features act as a line of defense against prying eyes. Your provider should offer these services to prevent hackers from accessing your personal data.
Round-the-Clock Network Monitoring
Cyberattacks don’t usually follow a certain predefined schedule; it is up to your web hosting provider to always stay alert. That’s the purpose of round-the-clock monitoring systems.
It’s like having a digital watchtower that monitors your website’s security, traffic, bandwidth, and other aspects and ensures there are no security loopholes cybercriminals can exploit. And if a loophole exists, this monitoring system fixes it immediately, leaving no room for cyberattacks.
Encryption
Encryption is when you conceal information by making it appear random and unreadable. Say, for example, you’re sitting in the front row of a classroom full of students. Someone hands you a note reading “You’re my best friend” and asks you to deliver it to the intended recipient, who is sitting in the back row.
Since the note will likely pass through many hands before it lands on the recipient’s desk, you decide to change the information to unreadable text, something like “dhh4 3#4 94 a2h4 4ahjd” (this is just an example and not how an encrypted message looks). Once the recipient receives the note, the text changes back to the original message, and they can read it. That’s how encryption works in a nutshell.
So, how do you find a web host that offers encryption? Look for features such as SSH and SSL:
- Secure Shell (SSH): This network passes the encrypted information from one point to another.
- Secure Sockets Layer and Transport Layer Security (SSL or TLS): You probably see this on a daily basis. It’s the padlock icon at the top left corner of your browser, right before the URL of the website you’re visiting (not all websites have it, though). It helps show that the communication between the website and server is secure.
This padlock icon, a universal symbol of data encryption and security, is also important for your business.
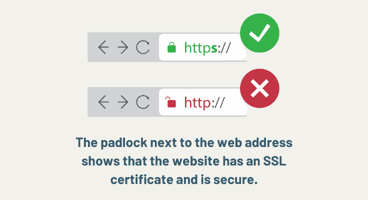
For perspective, our recent HostingAdvice survey of 1,055 US adults showed that 39% of people don’t trust a small business website that doesn’t use encryption2.
Secure File Transfer Protocol (SFTP)
To better understand what Secure File Transfer Protocol is and how it works, let’s rewind the tape to the classroom example I gave earlier. What would happen if you delivered the note to the recipient without encrypting the data?
Everyone would be able to read its contents. But that’s not even your biggest problem; the real concern here is that anyone with malicious intentions would alter the information. So, rather than reading “You’re my best friend” as intended, the note would have a different message, probably something mean, by the time it lands on the recipient’s desk.
Now think about the same scenario when purchasing a product online using your credit card. Secure File Transfer Protocol, as the name suggests, is a file transfer protocol that ensures that whatever information you share with the server passes through a secure network.
WHOIS Domain Privacy
When signing up for a web host, you’ll likely come across a section asking you to purchase WHOIS domain privacy protection at a small fee before you check out.
So, what exactly is WHOIS? The clue is in the name.
WHOIS is a public database that stores the information of anyone who registers a domain3. Since this data is open to the public, anyone can retrieve it and find your contact information. That’s likely one of the reasons you keep receiving scam phone calls and emails because someone had access to your private information when you registered your domain.
You should always add a WHOIS domain privacy subscription to your shopping cart to keep your domain private from prying eyes. It’s also good to understand local privacy laws in your country or wherever your website visitors are.
Examples of these laws include:
- General Data Protection Regulation (GDPR), which protects the personal data of people living in the European Union.
- California Consumer Privacy Act (CCPA) is a privacy law that requires web hosts to notify you about data collection and how they share it. It also stipulates that your web host must allow you to opt out of data collection.
- Personal Information Protection Act (PIPA) is a South Korean privacy law, similar to the CCPA, which requires web hosts to obtain your consent to collect personal information. You’re also able to access it and request security measures at any time.
Website security is a collective responsibility, but it’s worth the time you (as a business owner or user) and your web host invest in it. Your web host may have the latest security features installed on your server, but if you, as a client, don’t take the proper steps to protect yourself, you may end up being the weak link cybercriminals need to break through the security barriers.
Privacy Practices to Keep You Safe
Hackers don’t rest, and neither should you. Let’s quickly go over some tips on keeping your information safe from the prying eyes of cybercriminals.
Use Secure Passwords
It’s time to stop using your birthday or the last four digits of your phone number as your password or PIN. Using “Admin” isn’t safe either. Instead, consider using a secure password generator or a random sequence of numbers, letters, and symbols.
And don’t even think about recycling your passwords. Unfortunately, that’s a common practice.
More than 60% of Americans used the same password across multiple platforms, including their Gmail accounts, social media, and even online banking4.

If a hacker gets access to one of your accounts, they can easily log into others sharing that password. To be safe, use a secure password.
Consider a VPN
Virtual Private Networks are a great way to hide your information and online activity. A VPN conceals your IP address, internet traffic, DNS settings, and online footprints. But if you’re going to use one, make sure you only choose premium VPN providers.
Free versions may not be as secure. Others run targeted ads to support their infrastructure. But think about it for a minute, how would they know which ads to show you if they’re not monitoring your activities online? When all is said and done, free VPNs are unsafe.
The same applies to free web hosting services.
Our recent survey of 1,055 US adults found that 43% of people who searched for a web host were most interested in free hosting5.
We understand free services are tempting, but be careful about which services you sign up for.
Free hosting providers don’t usually have the security infrastructure to protect your site. Some will also run relevant ads on their platforms, the surest indicator that someone somewhere on the internet has an eye on every step you take.
Recognize and Avoid Phishing Attempts
Phishing is when someone tries to get your personal information, such as your Social Security Number, by posing as a reputable individual or a representative of a well-known company or organization.
You may get a phishing email from someone posing as your banking institution asking you to sign in to your account. But when you click on the link in the email and enter your login, that information is captured by hackers.

Here are some quick tips to help you recognize and avoid these scams.
- Phishing websites frequently use URLs that resemble legitimate ones but have slight variations, misspellings, or additional characters to trick you into thinking it’s legitimate. Pay close attention to the web address for any abnormalities.
- Watch out for unsolicited emails that try to create a sense of urgency or fear, especially if they ask you to verify account information, reset passwords, or provide sensitive data.
- Double-check the sender’s email address for any irregularities since phishing emails may use email addresses that look similar to legitimate ones but have small differences. The email may contain a noncustom domain, such as gmail.com.
- Never click on suspicious-looking links.
- Don’t download attachments from unknown sources. They may contain malware or viruses.
- When in doubt, verify with the company or organization directly through their official website or customer support before providing the requested information.
Above all, remember to trust your instincts. If something feels off or suspicious, don’t respond to the communication.
Audit Your Apps and Social Media Accounts
Social media is one of the most common targets for hackers. To protect yourself and your private information, consider replacing your social media passwords with secure ones.
Remember not to use the same credentials for all your social media accounts. That could grant the hacker access to all your accounts if they succeed in hacking one of them.
While these steps create a barrier between your personal data and bad actors, they aren’t 100% effective. Read our latest Master Cybersecurity Guide to learn more ways to protect your business (and yourself) online.
Do I Really Need Domain Privacy Protection?
When you register a domain name, the registrar collects your name, email address, phone number, and even your address to store in a public WHOIS database. We live in interesting times, and domain privacy protection is no longer a luxury but a necessity.
Without this protection, anyone can access your personal information from the WHOIS database. Domain privacy protection conceals this information by replacing it with fake contact information (or the hosting provider’s information).
Some of the risks of having your personal information in the WHOIS database include increased spam calls, phishing emails, and identity theft. But thankfully, domain privacy protection is inexpensive, and you can easily purchase a plan from your hosting provider.
How Does Encryption Work?
Encryption hides information as it travels from one point to another (typically between your local device and a server). Keep in mind that cybercriminals are always observing network traffic and information shared between the client and the server.
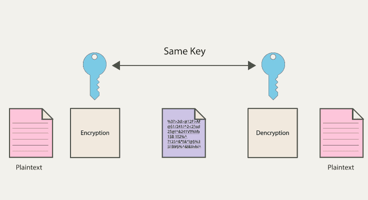
Take your login credentials as an example.
When you input these credentials on a website, they travel to the server for authentication. If the credentials match what is on file on the server, the site will grant you access to whatever information you need. This could be something as simple as logging into your Facebook account.
However, without encryption, the information that travels from you (the client) to the server is at risk of falling into the hands of other third parties while in transit.
To avoid this, encryption changes the information in transit into a format that is not readable and then makes it readable once it arrives at the intended destination. This prevents hackers from accessing your passwords.
What’s the Difference Between SFTP and FTP?
SFTP is when data travels from one point to another through a secure tunnel. On the other hand, FTP is when the same data travels without any form of security, making it vulnerable to attacks7.
The “S” stands for secure. You should always opt for a hosting provider that offers SFTP in lieu of FTP. It’s a simple measure to protect your website’s files in transit.
Interested in secure web hosting services? Here are our best picks.
What Does Network Monitoring Include?
Network monitoring in web hosting is when the hosting provider keeps an eye on various network components, such as:
- Availability of web hosting servers (uptime and downtime)
- Server resources such as CPU usage, memory usage, disk space, and bandwidth consumption
- Unusual or suspicious activity, such as DDoS attacks or unauthorized access attempts
- Website response times, page load speeds, and other performance metrics that impact user experience
- Status and validity of security certificates, such as SSL
That’s an overview of what network monitoring entails. Keep in mind that web hosting companies may offer additional monitoring services and technologies, which vary from host to host.
How Do I Create Strong Passwords?
Below are some rules for creating a strong password.
- Make it between 12 to 14 characters long
- Throw in a mix of uppercase letters, lowercase letters, numbers, and special characters (think random number and letters, such as 12DHi!@ylpL&)
- Avoid using common words, phrases, or easily guessable information like “Admin” “password,” “123456,” “qwerty,” or your cat’s name or your birthday
- Do not reuse passwords across multiple sites (this makes it easy for hackers to break in once they gain access to one account)
- Avoid using sequential characters like “abcd” or “1234” as they are frequently used and easy to guess
Besides setting up a strong password, whenever possible, enable two-factor authentication. This can help add an extra layer of security and keep hackers at bay.
You can also use a reputable password manager (but not a free one) to generate, store, and manage strong, unique passwords for each site you use.
Take Control Of Your Online Privacy and Security In 2024
Your online security is your responsibility. Only you can choose a web hosting provider that ticks all the right boxes regarding security. Also, you’re the only one who can make it even more difficult for hackers and other cybercriminals to access your information.
The tips I’ve shared here will add an extra layer of security over your private information as you browse the internet. If you’d like to learn more about cybersecurity, here’s the ultimate cybersecurity guide to get you off the runway.
Sources and Further Reading
1. Survey by HostingAdvice.com
2. Survey by HostingAdvice.com
3. https://whois.icann.org/en/about-whois
4. https://storage.googleapis.com/gweb-uniblog-publish-prod/documents/PasswordCheckup-HarrisPoll-InfographicFINAL.pdf
5. Survey by HostingAdvice.com
6. Survey by HostingAdvice.com
7. https://www.redhat.com/sysadmin/ftp-vs-sftp
Survey Methodology: A national online survey of 1,055 US consumers, ages 18 and over, was conducted by Propeller Insights on behalf of HostingAdvice in June of 2023. Survey responses were nationally representative of the US population for age, gender, region, and ethnicity. The maximum margin of sampling error was +/- 3 percentage points with a 95% level of confidence.







