
In today’s digital age, the internet has become a vital platform for businesses to thrive and, in turn, succeed. But as more companies establish themselves online, threats have, too: More than 800,000 cyberattacks are reported annually1.
The costs associated with cybercrime, are projected to reach $10.5 trillion by 2025, up from $3 trillion in 20152. These costs result from operational disruptions, legal expenses, and the expenses related to investigating and recovering data breaches.
The need for businesses to fortify their data online is more than necessary — it’s vital. But with hackers lurking in the shadows of the dark web, it can be hard to identify which features and add-ons are actually worth the investment.
And that’s where this guide comes in. With secure access, data protection, and threat protection, you can implement cybersecurity measures that protect against viruses, hackers, and breaches. But there’s a lot out there, so we’ve broken down each essential category and the extra features vital to safeguarding your website.
-
Navigate This Article:
Terminology Definitions
Before diving into today’s cybersecurity measures, you’ll need to understand some basic terms and their definitions. Here’s what we cover in our guide:
- Client: A device that requests services or resources from a server in a networked environment
- Cyberattacks: Deliberate actions taken to exploit vulnerabilities in computer systems or networks
- Cybersecurity: Measures and practices implemented to protect computer systems, networks, and data
- Cybercrime: Criminal activities conducted through computer networks or the internet
- Dark web: A part of the internet that is intentionally hidden and not easily accessible, often associated with illegal activities and marketplaces
- Hackers: People who have advanced computer skills and use them to gain unauthorized access to systems or networks to commit cybercrimes
- Network: A collection of interconnected computers, devices, or systems that can communicate and share resources, such as data, files, and services
- Protocol: A set of rules and guidelines that govern the communication between devices within a network
- Server: A system that provides services or resources to a client with the ability to host websites, store data, or manage resources
- Unauthorized access: Act of gaining entry without proper authorization or permission from the website or server administrator
- Web application: A software program that is accessed and used through a web browser, such as Gmail
Other terms will also be defined throughout this guide, especially if they’re security measures and tools worth looking into. Now that you know the essential terminology, let’s get moving!
Secure Access
Secure access is an umbrella term that refers to tools and features, such as authentication, SSH, SSL, and firewalls, that can protect data from unauthorized users.
Just as you would secure your house but provide the alarm code to your children, website security protocols verify the identity of users and ensure that they have the necessary permissions to access the website.
Must-know stats:
- The SSL certificate market is growing with a CAGR of 12.3% and is expected to reach $226 million by the end of 20263
- 43% of breaches involve web applications4, with information and technology being the most vulnerable5
- Only ¼ of people are required to use a password manager at work6
Without secure access, your website or business faces a greater risk of data breaches — which may lead to significant financial loss, reputational damage, and inevitable legal complications.
Think back to the 2017 Equifax data breach, which compromised the data of 147 million people. Hackers exploited a vulnerability in Equifax’s website application, allowing them to access Social Security numbers and credit card data. The breach would not have happened if Equifax had updated its web application firewall (WAF).
Authentication
Did you know the most common passwords are “guest,” “123456,” and “password”? Yes, really.
These passwords are obviously very guessable, which makes them an easy target for hackers and bad bots. To combat the use of weak passwords, many websites and online services implement specific requirements to strengthen passwords. Some standard criteria include longer passwords and a mix of different characters, like letters and numbers.

While these criteria are helpful for personal use, businesses are encouraged to take it further and adopt a password management system like LastPass and 1Password.
Companies like these are there to make your life easier (so you’re not forced to remember a dozen different passwords!). But they also prioritize security, centralized management, and meeting all local compliance requirements, including the guidelines laid out by the U.S. Department of Commerce National Institute of Standards and Technology (NIST) and the Federal Information Security Modernization Act (FISMA).
How Can I Keep My Business Passwords Safe? >>
SSH
SSH (Secure Shell) is a network protocol providing secure remote access and data communication over an unsecured network. It establishes an encrypted connection between a client and the server, allowing users to log into remote systems without issue. (If you’ve ever used a remote desktop, this is where SSH comes in handy.)
The latest standard for SSH is SSH-2, which is supported by the ever-popular OpenSSH and goes far beyond being the updated version of SSH-1. It’s a significant rewrite using encryption and authentication algorithms, including AES, Blowfish, 3DES, CAST-128, and RC4.
What’s the Difference Between SSH and SSL? >>
SSL/TLS
SSL (Secure Socket Layer) and its successor TLS (Transport Layer Security) are encrypted protocols to secure communications and sensitive data transmitted over the internet between clients and servers.

The latest version is TLS 1.3, which introduces security, privacy, and performance improvements, including enhanced encryption algorithms, perfect forward secrecy, and reduced handshake latency.
WAF
A WAF (web application firewall) is a security solution that protects web applications from cyber threats. It sits between the web server and the client, and analyzes incoming and outgoing web traffic for potential malicious activities.
What Types of Firewalls Are There? >>
Data Protection
Data protection is critical in maintaining data privacy, security, and accuracy. This method prevents unauthorized access and destruction via backups, recovery, and encryption.
Data protection is essential for establishing trust with customers, complying with legal requirements, and avoiding the potential financial, reputational, and legal repercussions of data breaches or unauthorized access.
Take your bank for your example: Per federal law, banks must employ various data protection strategies, including encryption, access controls, firewalls, patching, and disaster recovery.
Must-know stats:
- Every five years, 20% of medium-sized and small businesses experience data loss from a major disaster7
- 82% of internal breaches are caused by human error8
- 93% of companies that experience a significant data loss and do not have a plan for recovery will be out of business in one year9
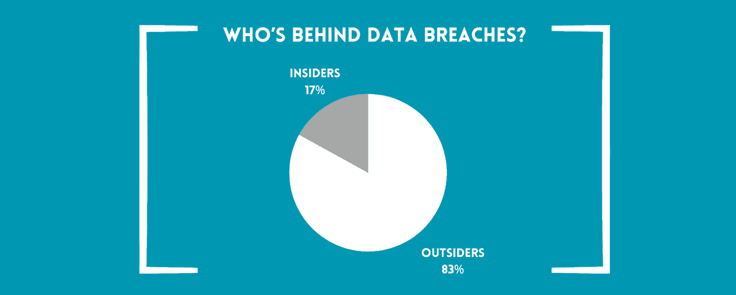
- Who’s behind data breaches? It’s 83% outsiders, and most are financial-driven10
From data breaches and identity theft to legal consequences and fraud, there’s a lot on the line when you don’t practice the right measures. And almost always, an unsecured data breach leads to customer churn, negative publicity, and damage to your brand reputation.
Take it from Target, whose 2013 data breach compromised the credit cards of more than 40 million customers. They know almost nothing is worse than being entrusted with sensitive data by your customers only to have poor protocols in return.
There are ways you can stay up-to-date on your data protection, and some of the most common and accessible ways are through regular backups, specialized encryption, and recovery methods, which safeguard against data loss and can help restore data after an incident occurs.
Backups
If you’ve ever used Microsoft Word, you have probably experienced this: You’re working on an essay (or perhaps the next Great American novel), and suddenly, the program freezes, and your computer crashes. Panic sets in, but you soon breathe a sigh of relief when you find your document has been automatically saved in a backup file.
And there you have the magic of backups.
Backups are copies of data created and stored separately from the source to prevent accidental deletion, data corruption, hardware failures, and cyberattacks. You can rewind time and restore your files as if the mishap never happened.
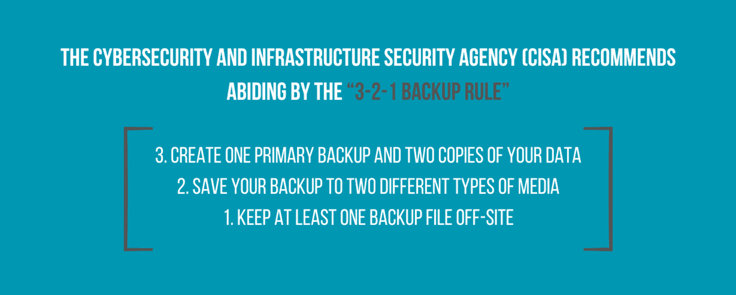
There are also different backups: Incremental backups only capture changes made since the last backup. Differential backups capture changes from the previous full backup, which takes up more storage space. Regarding our earlier example, Microsoft Word performed incremental backups.
Recovery
Data recovery is restoring lost, corrupted, or inaccessible data from hard drives (HDs), solid-state drives (SSDs), or backup systems. Lost or corrupted data might occur due to human error, server crashes, or cyberattacks.
If a company experiences a server failure and loses customer data, a recovery plan would come into play to restore that information. Without a recovery plan, all of that information could be lost forever — and when you’re dealing with something as essential as sensitive customer data, you’re bound to face legal and reputation repercussions.
While businesses aren’t legally required to have data recovery plans, some industries have rules. For example, HIPAA requires those in healthcare to have contingency plans. Many hosting providers also provide in-house or trusted third-party data protection so you can have peace of mind.
Encryption
Encryption is among the most valuable tools for data protection. It’s why you can use your credit card to buy something online without worrying about being hacked (that is if you’re buying from a trusted website!). Without proper encryption, anyone on the network could intercept and read your card number.
Encryption uses highly complex algorithms according to the Advanced Encryption Standard (AES), which disguises information into a scrambled code, called ciphertext, that only works between your web browser and the receiving server. This “code” now becomes unreadable to anyone who doesn’t have the decryption key.
Let’s say you’re buying something online with your credit card, whose number is 1234567891234567. To encrypt this number, your web app might use a substitution cipher based on a predetermined substitution rule, in which every number is encrypted by adding three random numbers between 1 and 9. So, your encrypted credit card number becomes 4728371497827417. (Don’t worry — real-world encryption algorithms are much more complex and secure than this example.)
Can Encryption Be Broken or Decrypted by Hackers? >>
Threat Protection
Threat protection refers to detecting, preventing, and mitigating cyberattacks, malware, data breaches, or other malicious activities that may compromise the security and integrity of computers, networks, and data.
Norton AntiVirus is an antivirus and security software solution designed to protect its devices. It can recognize real-time threats, including malware, viruses, and ransomware while performing automatic updates and web protection that may include the latest data backups, recovery, and encryption methods.
That said, threat protection is constantly evolving. But it is possible to stay one step ahead of cyberattacks and data losses through new technical solutions, consistent employee training, and the introduction of new security policies and procedures.
Must-know stats:
- Ransomware is the number one threat, costing $20 billion in global damages11
- In 2021, the average DDoS attack lasted 30 minutes; in 2022, it went up to 50 hours12
- Travel, retail, and financial services experienced the highest volume of bot attacks13
Your level of threat protection also depends on the type of devices you use.
For example, cross-platform compatibility may be necessary if you use several devices with different operating systems, like a Windows computer and an Apple iPhone. You’ll want to check out its security layers and advanced features when choosing a hosting provider with threat protection options.
Basic features may be SSL certificates and DDoS protection, but depending on the type of data you’re protecting, extra features beyond basic security, such as bot detection and malware detection, may be worth considering.
DDoS Protection
Distributed Denial of Service (DDoS) protection helps defend against DDoS attacks. DDoS protection uses several methods: traffic monitoring, anomaly detection, and real-time, round-the-clock monitoring.

A DDoS attack is a malicious attempt to disrupt a website, browser, or network by overwhelming it with illegitimate traffic from multiple sources.
Hackers will start by creating a botnet with several computers under their control to send a flood of requests or traffic to the target. The target system becomes overloaded and starts experiencing performance problems or complete unavailability.
What’s the Motive Behind DDoS Attacks? >>
Bot Detection
Have you ever visited a website and faced scrambled letters asking you to prove you were human? That’s CAPTCHA — and CAPTCHA is one of the best known ways web applications can identify humans from bots and reduce spam and cyberattacks.
But bots are getting smarter, so new measures are coming into existence that can better fight against them. To distinguish between human users and bots, dozens of bot detection software analyze user interactions, such as mouse movements, keystrokes, browsing patterns, and session behavior. Some automatic software systems also keep lists of patterns, unique identifiers, and addresses that help identify them. These databases help recognize and block bots when they try to access websites or perform specific actions.
If businesses produce effective bot detection measures, they can protect their websites and applications from various threats posed by bots, such as data breaches, fraud, content scraping, account takeovers, and disruptive DDoS attacks.
What Are Bad Bots vs. Good Bots? >>
Malware Detection
Malware detection is a set of techniques and technologies that identify, block, and prevent the effects of malware, which include viruses, worms, spyware, adware, and ransomware.
Malware detection software may use several techniques to detect potential threats adequately. Signature-based detection scan software identifies and compares its signature to known malware signatures. Application whitelists are also employed to maintain a list of approved applications and block everything else.

Today, with the rising use of AI and bots, many software uses machine learning behavior analysis. It’s based on artificial intelligence and machine learning (AI/ML) and helps existing security tools learn to differentiate between legitimate and malicious files and processes, even if they don’t match any known pattern or signature.
What If AI/ML Is Used for Malicious Activity? >>
The More You Know: Frequently Asked Questions
As we said, there’s a lot to cover, so we’ve compiled a list of frequently asked questions from our cybersecurity guide. If you’re ready to dive into the deeper end of cybersecurity, this section is for you.
How Can I Keep My Business Passwords Safe?
The National Cybersecurity and Communications Integration Center (NCCIC) monitors, responds to, and manages cybersecurity incidents. It recommends that users take the following actions to keep their passwords safe and choose good ones.
Avoid common mistakes like using personal information for your passwords or PINs. Unfortunately, this means not using everyday numbers that are easy to remember, like your birth year or “1234.”
NCCIC also recommends not using a word that’s in the dictionary. So instead of “ice cream” as your password, you could use something like “RRimf,” which stands for “Rocky Road is my favorite.” Combining uppercase and lowercase letters also adds another layer of security since passwords are case-sensitive.

NIST has a few guidelines that can help develop strong passwords. In essence, length and complexity are critical — the longer a password, and the more characters and numbers it uses, the better. (In fact, passwords between 8 and 64 characters are strongly recommended!) So instead of “RRimf,” you could choose “RRimf#gizmo46!” which combines your favorite ice cream, your neighbor’s dog’s name, and a random number accompanied by two special characters.
It’s tempting to reuse the same passwords for several accounts, especially if you’re creating lengthy and complex passwords that are hard to remember. But avoid doing this if you can: Even reusing a strong password endangers your accounts as much as using a weak password because if hackers get into one of your accounts, they can get into others, too.
What’s the Difference Between SSH and SSL?
Before we dive into the differences between SSH and SSL, we need to understand what a network stack is. Network stacks are like layers of blankets, each layer serving a different purpose.
Using the TCP/IP model, here’s each layer:
- Application
- Host-to-Host
- Internet
- Network Access
SSL and SSH operate at the Application layer, which uses encryption algorithms to secure data transmitted between network services and user applications, such as web browsers, email clients, remote desktops, or instant messaging apps. SSL and SSH aren’t mandatory (this is why you might see hosting providers advertising an included SSL certificate). Still, they’re crucial tools whenever sensitive data or privileged access is involved.
While they both involve encryption of sensitive data, they’re used in different use cases. SSL secures web communication and data transfers, while SSH is geared toward secure remote access and command executions.
Why Did TLS Replace SSL?
TLS replaced SSL because of security vulnerabilities discovered in previous SSL versions.
If you’re in the IT sphere, you may have heard about the POODLE, Heartbleed, and FREAK attacks, which decrypt previously encrypted sensitive data like login credentials, cookies, passwords, and private keys.

TLS was introduced in response to these attacks. TLS has stronger cryptographic algorithms and is constantly undergoing improved versions that address current vulnerabilities.
If you’ve never heard of TLS before, you may have noticed that many hosting providers only advertise SSL as a safety feature. But don’t worry: Since TLS is an upgraded “version” of SSL, these terms are often used together or interchangeably. In other words, hosts are offering TLS certificates but are just using the term “SSL” because it’s better known.
What Types of Firewalls Are There?
Firewalls are like virtual barriers that sit and monitor between a private internal network (like a company’s network) and the outside world (like the internet). Different types of firewalls cater to various security needs and deployment scenarios.
- Packet filtering: Think of packet filtering as a firewall that filters traffic at a basic level. It decides which packets, or data, are allowed to enter or leave a network based on information like source and destination addresses. It’s sort of like a bouncer checking IDs at the entrance to a bar.
- SPIs (Stateful Packet Inspection): SPIs are a step further than packet filtering. They not only look at individual packets but also keep track of the context of the packets and then allow or block traffic based on the history of the connection. It’s like a security guard at a top-security company who lets recognized employees enter and stops visitors for identification.
- Proxy server firewalls: Proxy server firewalls protect you from unknown people and secure your privacy. They hide your IP address, making it harder for attackers to identify and target you.
- Circuit-level gateways: These firewalls create secure tunnels for specific applications, allowing data to pass safely. But they have limited visibility into the content of the packets. Think of it as checking the tickets of concert goers without searching their bags.
- Next-generation firewalls: These firewalls offer application-level control (the top level of the network stack), meaning they can understand and control specific types of traffic, like web browsing or file sharing. They also have advanced features for threat detection and prevention. This is the top tier of security, similar to a presidential-level security guard who knows who’s coming and going and why they’re there.
- IPS (Intrusion Prevention System): IPS goes beyond basic firewall functionality. It monitors network traffic in real time, looking for signs of malicious activity. It can detect and prevent network attacks before they can cause harm.
Hosting providers that offer security packages often include built-in firewall capabilities, which could contain a combination of technologies like the ones mentioned above.
But as with anything, make sure you do your due diligence and find out what kinds of security features your provider offers — your needs may vary depending on what your business needs the most. For example, banks likely use all these firewalls, plus custom-made firewalls offering more comprehensive protection. On the other hand, personal blogs probably only use a basic firewall solution, like packet filtering.
What Do You Backup To?
You know that backing up your data is important, but where exactly do you back it up? Luckily, there are several options to choose from, and you can narrow down to the right choice based on your business’s data volume, budget, and material sensitivity. Here are some of the most common options:
- On-site backups: When you choose on-site backups, you store your backups on local servers on your business premises. This gives you direct access and control over your data, but it also means theft or damage is risky.
- Off-site backups: You keep your data in a different physical location, such as datacenters. This option is great for safeguarding against natural disasters or localized incidents that can harm your business premises.
- Cloud backups: Cloud backups are managed by a cloud service provider, which involves storing all your data virtually in the cloud. Many businesses opt for cloud-based solutions due to their flexibility, scalability, and the fact that you don’t need a physical storage location. Since your data is stored off-site, you can access it anywhere with an internet connection.
- Hybrid backups: Hybrid backup combines the best of both worlds. You can keep local backups on-site for quick data recovery when needed. At the same time, you can take advantage of the cloud for enhanced off-site protection. This ensures immediate backup access while benefiting from cloud storage’s added security and redundancy.
No matter which route you choose, having multiple copies of backups stored in different locations or mediums is always recommended to guarantee protection against potential threats or unforeseen circumstances.
What’s a Recovery Plan?
Recovery plans (business continuity plans) are strategies, procedures, and actions businesses take when a disruptive event — like a data breach — occurs. The primary goal of a recovery plan is to minimize financial loss and downtime.
Every business’s recovery plan differs, but some standard plans may include performing recent backups, hiring IT personnel, or working with a professional data recovery team.
The two latter options can become expensive, so performing several daily backups is always advisable for smaller businesses. In contrast, corporations with larger budgets may use in-house IT teams or professionals to help stay secure.
Can Encryption Be Broken or Decrypted by Hackers?
While encryption is designed to be highly secure and difficult to break into, there is no such thing as complete immunity. The ability to decrypt largely depends on the algorithm’s complexity, key length, computational power, and any potential weaknesses or vulnerabilities discovered in the encryption method.
For example, if an attacker attempts to gain unauthorized access to an encrypted database, they would have a hard time breaking through an encryption algorithm like AES with a 256-bit key. The combination of the algorithm’s complexity, key length, and the computational power required makes it impractical for them to hack into the server without raising suspicions first.
What’s the Motive Behind DDoS Attacks?
DDoS attacks can be used to retaliate, extort, or sabotage. It can even be used as a way to send a message.
Remember the “hacktivist” group Anonymous? In 2010, Anonymous launched Operation Payback. The goal of Operation Payback was to make a statement against perceived injustices and to demonstrate the power of online activism.
But usually, the singular goal is to cause service disruption and affect the reliability of significant companies and platforms.

In 2016, a massive DDoS attack was launched against Dyn, a major domain provider. Using a botnet composed of IoT devices, the attack compromised thousands of devices. It affected high-profile websites, including Twitter, Reddit, Netflix, Spotify, and The New York Times, and caused service disruptions and complete outages and resulted in financial losses.
The motive was unclear — but the attack caused one of the biggest DDoS attacks in history.
What Are Bad Bots vs. Good Bots?
Bots are part of automated software programs that interact with websites, applications, and online systems. Like any other resource, bots can be used for good or bad purposes.
Bad bots are used for malicious purposes and are often deployed by cybercriminals to perform cyberattacks. Bots can perform web scraping (illegally extracting data), DDoS attacks, spamming and malware, and credential stuffing (stealing usernames and passwords). Bad bots can also create a botnet, a network of compromised computers or devices under the hackers’ control. Botnets are often used in DDoS attacks since botnets can overwhelm servers with a flood of internet traffic all at once.

Good bots are part of our everyday lives. For example, good bots operate within search engines like Google and Bing, where they crawl and index web pages to create search engine results. You may also notice the work of feed aggregator bots, which collect and aggregate content from various sources to generate news or content feeds. Good bots can also mitigate against bad bots by identifying system weaknesses.
What If AI/ML Is Used for Malicious Activity?
Just as we have good and bad bots, hackers can leverage AI/ML for malicious purposes, which could lead to more sophisticated and mysterious attack techniques.
Of course, this is considered a misuse of AI and a problem cybersecurity professionals are aware of. That’s why AI and ML detect potential threats, whether AI-based or not.
To mitigate this potential threat, regularly updating security protocols and implementing multiple security measures, including detection techniques, behavior analysis, and human expertise, is crucial.
Secure Your Business By Defending Against Modern Cyberthreats
More than 80% of businesses14 have experienced hacking, which points to two clear conclusions: Malicious activity is becoming more aggressive and more intelligent, and the only way to fight back is to defend with the right resources. By implementing secure access, data protection, and threat protection measures, you can enhance the security of your business, safeguarding it from any threat that may come your way.
Further Reading and Resources
- https://www.securitymagazine.com/articles/87787-hackers-attack-every-39-seconds
- https://cybersecurityventures.com/cybercrime-to-cost-the-world-8-trillion-annually-in-2023/
- https://www.reportlinker.com/p05532153
- https://mobidev.biz/blog/best-practices-to-secure-web-applications-from-vulnerabilities
- https://www.embroker.com/blog/cyber-attack-statistics/
- https://bitwarden.com/resources/world-password-day-global-survey-full-report/
- https://www.enterpriseappstoday.com/stats/backup-statistics
- https://www.grcelearning.com/blog/human-error-is-responsible-for-85-of-data-breaches
- https://www.unitrends.com/blog/what-are-the-consequences-of-data-loss
- https://www.verizon.com/business/resources/reports/dbir/
- https://www.fortinet.com/resources/cyberglossary/recent-ransomware-settlements
- https://securelist.com/ddos-attacks-in-q2-2022/107025/
- https://www.imperva.com/resources/resource-library/reports/2023-imperva-bad-bot-report/
- https://cfosurvey.fuqua.duke.edu/press-release/more-than-80-percent-of-firms-say-they-have-been-hacked/







