TL; DR: Late last year, researchers in Germany discovered a vulnerability in content delivery networks (CDNs) known as the Cache-Poisoned Denial-of-Service Attack (CPDoS). In an extensive study of 15 web caching solutions, the researchers analyzed the impact of these attacks and provided appropriate countermeasures. Being that there’s no rest in the digital security space, the academics plan to continue working on solutions to mitigate such vulnerabilities as they grow increasingly complex.
These days, it seems there’s a dark side to nearly everything — including innovation. Cybercriminals are forever on the hunt for creative new ways to target their victims, making today’s threat landscape particularly menacing.
According to a 2016 report from Cybersecurity Ventures, cybercrime will cost the world more than $6 trillion annually by 2021. That’s more profitable than the global trade of all illegal drugs combined.
To combat this epidemic, researchers are looking to discover vulnerabilities — and disclose them to at-risk businesses — before criminals have the chance to cause harm. One such example is the Cache-Poisoned Denial-of-Service Attack (CPDoS), a newly discovered technique malicious actors could use to block access to web resources and sites.
Discovered by German researchers Hoai Viet Nguyen, Luigi Lo Iacono, and Hannes Federrath, and introduced on October 22, 2019, CPDoS is distributed via content delivery networks (CDNs) or housed on proxy caches.
Researcher Hoai Viet Nguyen (“Viet”) gave us an inside look at the CPDoS vulnerability affecting CDNs.
“By provoking an error on the origin server that is not detected by the intermediate caching system, the cache gets poisoned with the server-generated error page and instrumented to serve this useless content instead of the intended one, rendering the victim service unavailable,” the researchers explained in their research paper, “Your Cache Has Fallen: Cache-Poisoned Denial-of-Service Attack.”
CPDoS is particularly dangerous because the attack poisons the CDN cache, distributing error pages to edge cache servers around the world — potentially causing large-scale disruptions.
“Caching is a complex mechanism,” Hoai Viet Nguyen (“Viet”) told us. “It’s not well-understood by many CDN providers — there is a significant lack of knowledge. You should do a lot of testing before putting a website with caching into production to mitigate CPDoS and other cache-related attacks.”
The researchers have thoroughly analyzed the impact of these attacks and provided appropriate countermeasures via their white paper. Ultimately, however, there’s no rest in the digital security space, and the academics plan to continue working on solutions to protect organizations from these vulnerabilities as they evolve.
Discovering the Cache-Poisoned Denial of Service
Viet told us that his research team stumbled upon CPDoS by accident. “We were already doing a lot of research in caching and CDNs, and one day, when I looked at the documentation of the Amazon CloudFront CDN, I found that they cached the inappropriate error code 400 Bad Request by default and had a very big header size limit.”
After some experiments, the team discovered that they could trigger an error page by sending an HTTP request containing a malformed header. After the error page gets stored by the caching server, it can be spread to multiple edge nodes in a geographically dispersed network, leading to a wide-scale denial of service.
In addition to warning CloudFront about the threat, the researchers also made Akamai, CDN77, Fastly, Cloudflare, and Varnish aware that their CDNs were also vulnerable.
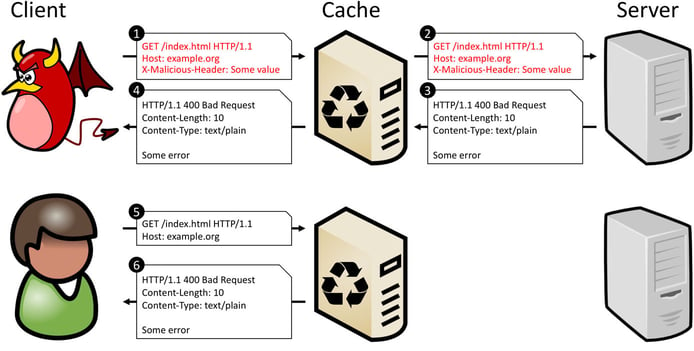
In a CPDoS attack, a malicious actor can block any web resource hosted on proxy caches or distributed via CDNs.
In all, three variations of CPDoS attacks exist: HTTP Header Oversize (HHO), HTTP Meta Character (HMC), and HTTP Method Override (HMO).
The HHO CPDoS attack exploits the variation in size limits for HTTP request headers, which contain essential information for web servers and intermediate systems. In this scenario, a cybercriminal can attack a web application that uses a cache which accepts a larger head size limit than the origin server. The server will block the request, causing an error page to be stored by the cache and spread via all requests thereafter.
Rather than send an oversized header, the HMC CPDoS attack bypasses a cache with a request header using a harmful meta character — such as /n, /r, or /a — to trigger an error page. The final variation of CPDoS, the HMO attack, works in scenarios where intermediate systems block specific HTTP methods.
An Extensive Study of 15 Web Caching Solutions
In “Your Cache Has Fallen: Cache-Poisoned Denial-of-Service Attack,” Viet and his fellow researchers detail the results from their February 2019 experiments on 15 web caching systems: Apache HTTP Server, Apache Traffic Server, Nginx, Squid, Varnish, Akamai, Azure, CDN77, CDNsun, Cloudflare, Amazon CloudFront, Fastly, G-Core Labs, KeyCDN, and StackPath.
Ultimately, the researchers found that different pairs of web caching systems and HTTP implementations (such as ASP.NET, IIS, Tomcat, and Amazon S3, among others) led to vulnerabilities in various CDNs. CloudFront was by far the most affected, with HHO, HMC, and HMO vulnerabilities across different platforms.
Since being notified of these vulnerabilities, Viet said the affected companies have taken measures to mitigate CPDoS attacks, and the majority of problems have been addressed (though some organizations were faster to act than others).
This is reassuring, considering the impact CPDoS attacks could have when used for malicious purposes.
“CPDoS can be used to block mission-critical sites, such as government websites and online banking, disable catastrophic warning information, or block patches and firmware updates distributed via caches to prevent vulnerabilities in software and devices from being fixed,” Viet said. “There are a lot of things a malicious actor could do to sabotage a website.”
Actively Researching Options to Mitigate Attacks
Fortunately, the researchers have identified a number of measures that content providers can take to protect users from CPDoS attacks. The first step in avoiding an attack is to cache error pages in accordance with HTTP standards.
“A lot of CPDoS attacks, and other cache-based attacks, result from the issue that the CDNs and caching providers do not honor policies and specifications,” Viet said.
For example, web caching standards dictate that content providers can only cache the following error codes: 404 Not Found, 405 Method Not Allowed, 410 Gone, and 501 Not Implemented. In many cases, vulnerabilities in the researchers’ experiments were caused by default error codes such as 400 Bad Request.
Providers can also exclude error pages from caching or deploy web application firewalls in front of the cache.
Moving forward, Viet said the research team will be working on additional approaches to mitigating CPDoS attacks as threats become more sophisticated. They are always evolving: For example, in March 2019, Nathan Davison detected a new variation using CORs headers, and in February 2020, he introduced another new variant affecting the CloudFoundry GoRouter.
“We have already suggested several solutions for how to mitigate these attacks in our research paper, but in the future, we will need to provide many more solutions as the attacks will become more complicated to take on,” he said.
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

