TL; DR: Featuring a cloud-based security platform leveraging futuristic artificial intelligence and machine learning, Wallarm protects applications and APIs with unrivaled accuracy and transparency. The web application firewall automates security and vulnerability testing to identify relevant threats and provide real-time safeguards for an organization’s most important online creations. By covering an application’s entire lifecycle and reducing the number of false positives, Wallarm enables customers to save time and explore integrating cutting-edge technologies into their stack.
Whether it’s a simple antivirus program for your laptop or enterprise-grade protection for mission-critical applications, a major hallmark for strong security programs is frequent updates and deployments that stay ahead of known threats and vulnerabilities.
These new releases often happen once a week, or even daily — and to Wallarm, that still isn’t good enough. In fact, it’s part of the problem, according to Chief Marketing Officer Renata Budko.
“Even in the current state of security, the average time between when a breach or vulnerability occurs and when it’s actually found is almost two months — 53 days on average,” she said. “Those companies manage to put out seven or eight new releases that introduce whole new sets of vulnerabilities before finding the one they unknowingly released two months ago.”
Wallarm instead automates daily security maintenance and updates, relying on cloud-based solutions backed by artificial intelligence and machine learning that identifies, evaluates, and reports new threats as they happen.
Founded in 2016, the company has already attracted top-rate customers like Automattic, Parallels, Acronis, and SEMrush. Whether organizations are developing apps in a public cloud or running established systems in private datacenters, Wallarm is ready to provide real-time protection.
“Wallarm starts detecting issues before the application even gets released,” Renata said. “It’s 360-degree security from when the tool is being developed to when it’s out there, or when something is going on in one of the modules. We do this from cradle to grave.”
Wallarm’s Cloud-Based Security Boosts Accuracy and Agility
False positives, or when a security system alerts admins about a problem that doesn’t actually exist, are surprisingly common among Wallarm’s competitors and can sap countless hours away from engineering teams, according to Renata.
“What it means to them is they need to drop everything to go and check the configuration, try to find the root cause, spend ungodly amounts of time and money,” she said. “Or, worse, they block an entire set of customers, lose money, and they lose reputation. It’s a very bad situation.”

Wallarm offers application security that stays ahead of emerging threats, according to Renata Budko.
By examining each API call with constantly adapting and evolving artificial intelligence and machine learning engines, Wallarm greatly reduces the rate of false positives. Even better, Renata said, the platform evaluates the detected vulnerabilities in terms of relevance and severity.
“It’s not just that we have very low false positives,” she said. “When we see something that is an attack, we know it’s bad. But do we know if it’s relevant to a specific application?”
For example, Renata described the recent outbreak of a fungus that made pine trees lose their needles and die.
“It’s a bad situation, no doubt,” she said. “But if you have an almond orchard, is it dangerous to you? Probably not, but it’s worth keeping an eye on.”
Instead of “waking up the IT admins in the middle of the night” when Wallarm flags an attack, Renata said the platform checks the threat’s relevance by removing any dangerous components and neutralizing the intrusion — then tries to attack the customer’s application with the same vector.
“If we see that nothing bad happens, the application doesn’t have a vulnerability, and you’ll see the incident in a report at the end of the month,” she said. “It doesn’t figure into our alerts, doesn’t show up flashing in red in your dashboards, and bells don’t start going off telling everyone to get to the office to deal with it.”
How it Works: Increasing Precision Via Machine Learning
The Wallarm platform comprises three components working together to produce continuous and automated application security: real-time protection, threat verification, and AI behavioral analytics systems.
For real-time protection, Wallarm nodes are deployed locally to inspect traffic and block malicious requests while the company’s cloud security tools house the AI components that create customized security rules for the application and its APIs.
“We start from a fairly good understanding of what can be attacked because we have a cloud that is always learning from hundreds of customers,” Renata said. “Even from Day Zero, our system already has a better rate of false positives than anything else out there because it has already learned from our other users.”
The platform then deploys active threat verification processes that disarm attacks and replays them in a safe way to see if any of them could have resulted in a security breach or other incident. If the scanner identifies any vulnerabilities, Wallarm creates a ticket and notifies the customer of relevant details.
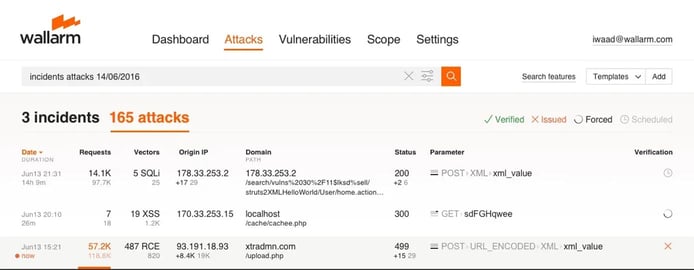
Wallarm learns about the structure and behavior of an application to detect what anomalies may actually be attacks.
Wallarm features three layers of machine learning, which runs continuously to adapt to changes in the customers’ applications without the need for manual reconfiguration. Based on live traffic, the algorithms reconstruct the business functions and application structure, learn data formats and parameters, and identify typical user behaviors and usage patterns.
“We’re able to use machine learning to deconstruct the logic of the application, even when it’s undocumented,” Renata said. “That’s how we’re able to detect exactly what is an attack with great precision.”
Anticipating Customer Needs and New Technologies
As enterprise IT and architectures become increasingly dynamic, Renata said keeping security consistently maintained and configured becomes more and more difficult. As such, Wallarm appeals to multiple levels of employees within an organization. While security engineers and other IT administrators appreciate the low rate of false positives, the agility and acceleration that Wallarm offers its customers is what appeals most to CEOs and CTOs.
“With us, security falls in step with agile development,” Renata said. “Instead of being an impediment to moving faster, digital transformation, and delivering the newest and best customer-focused applications out there, security now helps to deliver that — not slow it down.”
Wallarm employees talk with customers at least four times a year to learn about their needs, how the platform can improve, and emerging technologies the team may want to integrate.
“Even when they’re just looking into new architectures, they can log into a beta stage to test and make sure their security works with the latest and greatest thing they’re looking to deploy,” she said.
Because Wallarm’s platform automatically creates and learns new rules, she added the platform is extremely flexible and adaptable to new technologies and infrastructures. Last year, Renata said the hype was around Docker containers; this year, it’s Kubernetes.
“Other solutions are fixed,” Renata said. “You can’t really move to a new architecture without forklifting it out and putting something entirely new in. Most importantly, Wallarm moves with the infrastructure. You can do what’s best for the business and not worry about having to retool the entire security chain.”
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

