
TL; DR: Whonix protects user anonymity by routing internet connections through Tor’s network of volunteer-run servers while deploying advanced security mechanisms. The Linux-based OS, which runs on top of existing systems via virtual machines, can be installed on Windows, macOS, and Linux. Moving forward, the Whonix team plans to release a version of its OS that can be installed directly on a piece of hardware for those looking to maximize privacy and security outside of a VM.
Since 2002, journalists, hacktivists, and government whistleblowers — among others looking to protect sensitive data and circumvent censorship — have turned Tor’s open-source network of proxy servers to enable anonymous communication online.
The technology works by transferring data in encrypted packets across thousands of randomly chosen, volunteer-run servers, known as relays. This process hides the user’s location and makes it quite difficult to trace internet activity. That said, Tor cannot promise bulletproof anonymity — at least, not on its own.
Although the odds of such an occurrence are low, the IP addresses of Tor users have been exposed in several instances over the years due to vulnerabilities impacting the Tor Browser Bundle. That’s where Whonix comes in.

Whonix protects user privacy by preventing IP leaks.
When installed on top of Windows, macOS, or Linux, the VM-based operating system’s security-hardening features protect users from IP leaks — even in the face of viruses designed to bypass Tor’s proxy servers. In addition to forcing internet connections through Tor’s proxy server network, Whonix employs compartmentalization to provide a private, leak-resistant computing environment.
“I started Whonix after research began coming out on the security limitations of traditional operating systems,” said Patrick Schleizer, Founder of Whonix. “Its disaggregated design, which splits Tor into its own virtual machine while sandboxing user activities into another that cannot connect to the network, seemed like the natural next step in providing better security assurance.”
Today, users around the world rely on Whonix to preserve privacy and anonymity online. As for what’s ahead, Whonix is poised to welcome an even broader user base, with plans to release a version of its OS that can be installed directly on hardware instead of a VM.
Empowering Windows, macOS, and Linux Users to Run Apps Anonymously
From the start, the Whonix team found itself one step ahead in the security industry. Indeed, the software was already on the market in 2013, when former CIA contractor Edward Snowden exposed top-secret NSA information about mass surveillance practices in the U.S.
“The Snowden revelations came out early in Whonix’s life,” Patrick said. “At the same time, we saw that advanced adversaries were using weak system security as an Achilles’ heel to bypass encryption and privacy,” Patrick said. “This really validated our effort.”
Whonix also witnessed the 2018 disclosures of Spectre and Meltdown, two related speculative execution attacks that exploit critical vulnerabilities in processors to steal data. “The disclosure was a major happening in the software world,” Patrick told us. “It exposed both how fragile end-point security is and issues with legacy and proprietary hardware platforms.”
The OS acts as an extra cloak of anonymity on top of the Tor network.
Both events broadened public awareness of the internet’s complex threat landscape, driving demand for transparent, open-source solutions like Tor and Whonix.
Whonix, of course, is a strong proponent of the open-source software movement. According to the project’s website, its developers consider it immoral to benefit from free software without giving back. In addition to the rewarding experience of keeping code accessible for public benefit, volunteering on the Whonix project helps individuals sharpen their skills and become more valuable employees. But it’s not always easy to attract new contributors.
“People now have generally become more privacy-aware than ever before — which is great,” Patrick said. “However, there is always more we can hope for in terms of manpower and contributions from the open-source coding community.”
Fueling Advanced Security via Open-Source Contributions
According to Patrick, the youngest generation of tech-minded graduates is often focused more on earning top-dollar salaries than on contributing to the open-source movement, and for good reason.
“They expect to be paid for finding bugs, rather than fixing them without charge to contribute back to the open-source community,” he said. “This is due to increased government and corporate demand for ethical hacking and security solutions combined with growing financial pressure on recent graduates.”
Those looking to get involved with the project have numerous opportunities to do so. Contributing developers with backgrounds in Linux are needed to squash bugs, perform audits, and maintain documentation, among other general tasks.
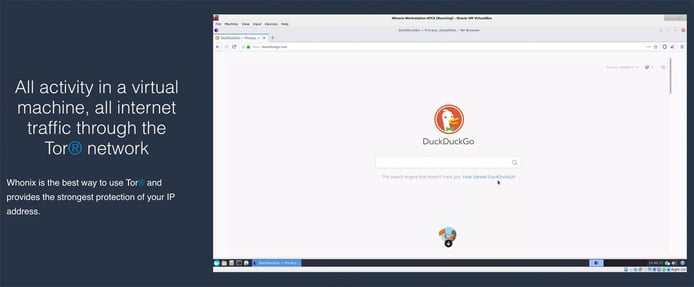
The technology uses compartmentalization to limit access to information.
Regular users and those without coding skills can also contribute by sponsoring a new feature, paying for priority support, or just spreading awareness about the technology via social media. Every contribution will help further Whonix’s mission to enhance the user experience so that anyone — from espionage targets to average computer users in repressive or censored environments — can benefit from the technology.
“Our main goal is to provide secure defaults that are transparent to users,” Patrick said. “You don’t have to be an iptables expert to avoid catastrophic traffic leaks that can expose your identity — we have you covered. Even if you get infected somehow, you are still safe (as long as the hypervisor is not vulnerable).”
Patrick told us all of the settings needed to make software in a separate VM talk to Tor in another is ready to go out of the box. “This relieves users from encountering issues in running Tor over Tor,” he said.
Community-Fueled Development and a Focus on UX
As an open-source project, all continuing development on the Whonix operating system originates from the community.
“Everything happens in an organic manner on our forums,” Patrick said. “Users and volunteers suggest ideas, and we discuss their merits and the best approaches to implement them. We then test new features before incorporating them in our stable version.”
Every new feature suggestion is carefully considered in terms of usability and informed by the security world’s latest developments.
“The main challenge we face is making the UX more comfortable for less experienced users,” Patrick said. “We want to welcome as many users as possible. As the adage goes, anonymity loves company. The more people we can get to use these systems, the larger the group will be for vulnerable people to hide in.”
Over the years, the Whonix community has worked hard to implement design features based on the latest usability research. It has also worked to create comprehensive operations security (opsec) documentation to bring users up to speed on internet security. After all, Whonix helps support anonymity, but online safety is ultimately a product of behavioral change.
Beyond the VM: Upcoming Host Distribution Solutions
Realizing that not every individual or business wants to utilize a virtual machine, the Whonix community is currently at work on a Whonix Host, which can be installed on a piece of hardware.
“We are planning for an eventual release of a Whonix Host distro that users install on their machines so that the security and privacy benefits we’ve developed over the years can be applied outside of the VM,” Patrick said.
The solution will further harden the security of the Whonix system.
“Privacy will be a central design aspect of this host system rather than an add-on that’s bolted onto proprietary operating systems.”
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

