TL; DR: Patchstack, formerly known as WebARX, helps developers shield web apps from third-party code vulnerabilities through a cloud-hosted patching platform, bug bounty program, and vulnerability database. The company recently completed an extensive rebranding effort to narrow its focus on third-party code security. Through its all-new brand, Patchstack’s goal is to foster a strong community of developers to take command of what has become one of the most significant website security issues of our time.
On February 10, 2021, W3Techs announced that WordPress had reached a noteworthy milestone: it now powers 40% of the world’s websites. That’s two out of every five websites in existence today.
The content management system (CMS) is the most popular solution of its kind for a reason. WordPress is free to download and use, SEO-friendly, and customizable via numerous add-ons. Specifically, over 58,000 plugins and 8,000 themes are available to extend functionality and change the look and feel of WordPress sites.
But the very quality that makes the CMS so valuable also makes it susceptible to threats. Research has shown that 55.9% of the attacks made on WordPress sites can be attributed to plugins and themes alone. Add in core platform vulnerabilities and themes, and the problem gets far worse.

Oliver Sild, Founder and CEO, gave us the scoop on Patchstack’s new image and focus.
That’s where Patchstack comes in. The cybersecurity company, based in Estonia, helps web developers secure web apps from third-party component vulnerabilities.
“We are not the only company working in the security ecosystem, but we are likely the most committed to solving the plugin security issue,” said Oliver Sild, Founder and CEO of Patchstack. “We are not only helping website owners patch their sites. We are actively trying to find vulnerabilities within plugins so they won’t get to our customers’ sites in the first place.”
Users may already know Patchstack as WebARX. The company announced a full rebranding in February 2021 to reflect an increased focus on third-party code security. The rebranding effort also follows the company’s January 2021 acquisition of the WordPress security company ThreatPress and the introduction of new services, including plugin audits.
From Website Development to App Defense
Before jumping into third-party code patching, Oliver founded a small, security-minded web company focused on Joomla, WordPress, PrestaShop, and Magento development. The common thread between the sites was that they all relied heavily on plugins, themes, and other add-ons.
“At first, we were working mostly on Joomla sites,” he told us. “I vividly remember the point in time when we had gotten used to building sites in Joomla, and then, suddenly, everyone was asking for WordPress sites.”
The team quickly realized that there were more security issues with WordPress than Joomla due to the abundance of third-party code available for WordPress sites.
“At that point, there wasn’t a product on the market that addressed component security,” Oliver said. “We built an internal tool to monitor all the different components we were using for our web development services and alert us to new vulnerabilities. In doing so, we realized the magnitude of the issue and decided to pursue resolving it.”
The team officially launched the product in 2018 after building a successful external prototype of the cloud-hosting patch platform the company offers today.
“The idea was to give web developers an understanding and an overview of the vulnerabilities that can be introduced to the site through third-party code, whether that means plugins, themes, or external snippets. Now, we have increased our focus on third-party vulnerability issues even more.”
The First Open-Source Bug Bounty Platform for Components
Today, Patchstack takes a three-pronged approach to helping developers shield web apps from third-party code vulnerabilities. In addition to its cloud-hosted patching platform, the company now offers a WordPress bug bounty program and is actively building a vulnerability database.
“We have almost 1,000 researchers signed up for our Patchstack Red Team, which is somewhat like HackerOne but only meant for WordPress plugins,” Oliver said. “We are basically paying for the researchers to find vulnerabilities within the third-party code people are using on the websites. This information will be made available to the public through our vulnerability database.”
The Patchstack platform provides virtual patches for plugin vulnerabilities that work to eliminate security risk without changing the website’s code.
“Once you connect your site to our software, we detect what kind of third-party code is installed,” Oliver said. “A lot of people aren’t aware of what is there. Then, whenever a vulnerability is found in a plugin, theme, or the WordPress core, the platform automatically applies virtual patches to your site.”
The platform takes into account what version of WordPress a site runs to avoid overloading the site with unnecessary rules. “This makes it stand out in terms of performance, as well,” Oliver said.
With this three-part approach, Patchstack not only improves the websites of its customers but the safety of the internet as a whole. Oliver told us that, as the cofounder of a coworking space in Estonia, community-building comes naturally.
“I’m also one of the leaders of a cybersecurity community in Estonia,” he said. “We’ve been doing Capture the Flag (CTF) competitions for almost three years now, so tapping into the community aspect of the WordPress ecosystem just makes so much sense. When it comes to security, we can do so little alone.”
Deepening the Focus on Third-Party Code Vulnerabilities
Oliver said that Patchstack’s narrowed focus on code vulnerabilities — a product of the rebranding — will only serve to make the company’s offerings stronger.
“Previously, we were more focused on generic tasks like filtering traffic, analyzing activity logs, and hardening sites through two-factor authentication (2FA),” he said. “With the rebrand that we are currently undergoing, we’re making sure vulnerabilities won’t get to our customers’ sites in the first place. We help them fix them before they even become a public matter.”
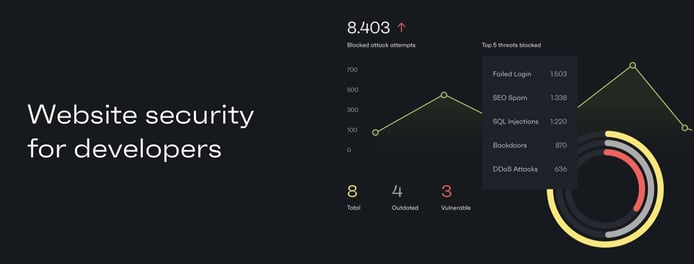
Patchstack helps teams identify potential security risks and vulnerabilities.
According to Oliver, third-party code security is the single most significant issue the WordPress community currently faces.
“Being completely focused on that problem allows us to provide the best solution possible,” he said. “We’re on a mission to fix one single problem, and that’s protecting the websites from the vulnerabilities that are introduced through plugins and themes.”
Building a Community and Growing Beyond WordPress
Moving forward, Patchstack’s goal is to keep building a community around its Patchstack Red Team and vulnerability database.
“When we look into the future, I think the community aspect of our company will become a bigger part of what we do,” Oliver said. “With our Patchstack Red Team, security researchers not only get credit for finding vulnerabilities, but they also get paid. At the same time, our open database is now available for all vendors, hosting companies, and the general public.”
Ultimately, the company can better serve its customers by combining the value garnered from both the database and the community into the Patchstack platform.
By the end of the year, Patchstack will begin expanding its platform to provide virtual patching for other popular site-building platforms.
“We are not stopping with WordPress,” Oliver said. “After Magento, Drupal, and Joomla, we can only go further and apply this to the whole PHP ecosystem and then move to JavaScript and so forth. The idea is to scale the platform so it applies to other technologies that have the same issues.”
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

