
TL; DR: Since 1998, Akamai has engineered performance and security solutions, now serving up two trillion Internet interactions daily. With the rising scale of DDoS attacks, defense and web application protection should be of utmost concern to companies. Today, launching a DDoS attack requires little-to-no technical know-how, and national governments are capable of launching “mega attacks” (100+ Gb/s) well beyond the scope of most protection systems. These factors, combined with the anonymity of Bitcoin, construct a dangerous web environment. Akamai and Trustwave have partnered to bring Akamai’s DDoS solutions and Trustwave’s forensic analysis into a complete protection solution.
As the web hosting community becomes more susceptible to increasingly-prevalent external attacks, there is a growing need for proactive measures to be taken in defense of a safer Web. With Internet security powerhouses like Akamai Technologies and Trustwave Holdings Inc. combining forces, customers are better shielded from cyber crime, despite the burgeoning challenges faced by cyber security officials.
Some Background on Akamai

Dan Shugrue, Akamai Director of Product Marketing for Security Solutions
Akamai began with its founders, Tom Leighton, Daniel Lewin, Randall Kaplan, and Jonathan Seelig, essentially screwing together the back panels of servers and co-hosting them in Internet service provider (ISP) spaces.
Today, Akamai has built 170,000 servers across 102 countries, in 1,300 different networks. They serve up 25 terabits of traffic per second, culminating in two trillion Internet interactions every day.
The scale of Akamai’s coverage is astonishingly huge. 85 percent of the world’s Internet users are within a single hop of one of their servers and they provide high-performance DNS and IP acceleration in addition to their well-know CDN services. DDoS and vulnerability protection are a growing business sector in the hosting space and, as usual, Akamai is at the forefront.
We got a chance to sit down with Akamai’s Director of Product Marketing for Security Solutions, Dan Shugrue, to discuss the growing need for DDoS defense, the infrastructure required to scale out Akamai’s massive server network, and their most recent strategic alliance with Trustwave.
State of the Internet: Growing Need for DDoS Protection
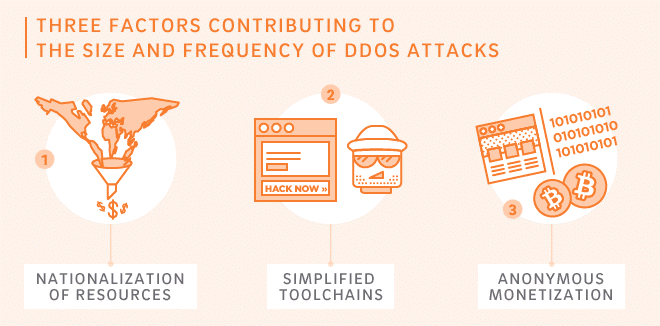
The nationalization of resources, industrialization of tools, and monetization all result in more DDoS attacks.
According to Akamai’s latest State of the Internet Security Report, the number of distributed denial-of-service (DDoS) attacks recorded on Akamai’s network has more than doubled over the course of a year (116.5 percent increase in total DDoS attacks in Q1 2015 compared to Q1 2014), and an over 40 percent increase in average duration was reported (24.82 hours in Q1 of 2015 compared to 17.38 hours in Q1 2014). According to Dan, the largest attack recorded by Akamai was about 320 gigabits per second last year, but a “mega attack” is defined as any incoming attack of 100 or more gigabits per second. He explained three main factors that contribute to these attacks’ growth in scale and frequency:
1. Nationalization of Resources:
The GDP of governments fund attacks, far outpacing the financial resources of even the largest company or crime syndicate. Dan explained that the most involved nations also tend to be the most industrialized, as well as those made famous in the media by political turmoil or upheaval. China’s “Great Cannon,” Iran’s DDoS on U.S. sites, and the UK’s attack against Anonymous are just examples made known to the public.
2. Simplified Toolchains:
These tools follow the same technological progression as computing in general. Becoming a “Power Chaotic Actor” on the Internet no longer requires hacking abilities or coder skill, according to Dan. Instead, someone looking to wreak havoc on the Web can use a graphical-user-interface-(GUI)-based application to launch an attack, or pay by the hour through a Hacking as a Service provider. Often times, someone can use load testing software and websites to launch automated visits from around the world, which will quickly swamp an unprotected web server. “There’s just lots of resources in the Dark Web and the Under Web to run these types of attacks,” Dan said.
3. Anonymous Monetization:
The rise of Bitcoin has permitted malicious external forces to demand ransom in exchange for returning stolen data, or decryption of a site. Dan used CryptoLocker, a particularly devastating string of malware, sometimes referred to as “ransomware,” as an example. CryptoLocker allows the chaotic actor to remove and encrypt data from a site anonymously, and then demand a Bitcoin transaction in exchange for the site’s safe decryption. “There’s no way to track it,” Dan explained, “so as Bitcoin has become more valuable, or more prevalent over the last 18 months, we’ve seen a lot more of those kinds of attacks.”
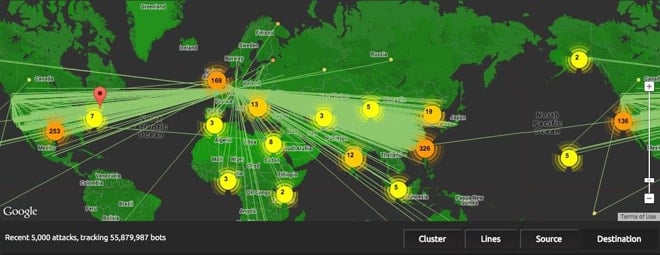
Global Map of DDoS Attacks in Real-Time
How Akamai Battles Attacks: Tons of Servers and Smart People
Since Akamai’s founding 17 years ago, they’ve served a myriad of technological purposes: optimizing routing, port control protocol (PCP) fast-starts, caching, static and dynamic content provisions, et cetera, but they also offer website protection. “Performance and protection go hand in hand,” when it comes to the Content Delivery Network (CDN), according to Dan. “We’re building out all of these servers to help distribute content around the world,” he said. “Those servers become a natural ‘moat,’ if you think about it in a defense analogy.”
Akamai’s Server Infrastructure
Like most CDNs, Akamai delivers content from an edge server closest to the origin, reducing the load to the origin’s infrastructure before the requested information reaches the end-user. While Akamai offloads from the origin (the website or hosting provider), the same rules can be applied if the requester of information happens to be a malevolent source. In this way, Akamai can use their massive bandwidth and server resources to ward off small- and large-scale attacks.
“Scale and size in DDoS attacks is really the beginning and the end of the conversation,” Dan said. “If you have a lot of machines, you can absorb really big attacks.” Of course, this is easier said than done. “It takes a ton of hardware and security know-how,” Dan said.

Akamai’s network features 170,000 servers in 102 countries, serving up data at speeds of 25 terabits per second.
Akamai’s Experienced Team
As one might imagine, it’s extremely difficult to find hyper-intelligent individuals who are well-versed in security matters. While plenty of companies may understand the need for a web application firewall (WAF), and maybe even purchase one, they then struggle with configurations, as well as maintaining and keeping track of the updates, let alone configuring a protection policy for the application. This is where strategic partnerships, allegiances, and corporate acquisitions become crucial to maximizing Akamai’s service offerings.
About a year ago, Akamai acquired Prolexic, a leading provider of Cloud-based security solutions for DDoS threats. Dan explained that this deal promised not only another defense network with a protection rate of multiple terabits per second, but also an army of highly-intelligent industry leaders who have been meticulously tracking the growth of these attacks in order plan their expenses. “So we can not only use that for capacity planning, we can also use that to share with our customers,” Dan said.
Akamai’s New Products to Bring to Market
Akamai has done a lot to develop their security practices, according to Dan. “We just finished a very successful paid beta program from our flagship security product, which is KONA Site Defender,” he said. Many customers have already bought into this managed KONA service, which offers unlimited updates to your WAF configurations, periodic threat assessments and reviews, and 24/7 monitoring. “The 24/7 eyes on glass is a big deal to a lot of customers,” Dan explained. “They want a human being letting them know what’s happening on their network.”
Looking towards the future and Akamai’s long-standing investment in a faster and safer web environment, Dan told us about one of the innovative inbound services Akamai offers. “We are investing heavily in our security business,” he said. “We’ve just come out with an IP reputation service, called Client Reputation.” With this new product, customers are able to choose to either accept or deny all requests from an IP address based on the activity of that IP.
Strategic Partnership: Akamai & Trustwave
The latest Akamai news for 2015 revolves around their most recent strategic alliance with Trustwave Holdings Inc. “We here at Akamai feel like we’ve been doing well with the security know-how, but the truth is, demand is outpacing supply, so if we can make a partnership with someone like Trustwave, then we’re better off, and our customers are better off,” Dan told us.
We also spoke with Trustwave’s SVP of Product and Corporate Marketing, Steve Kelley, who shared his thoughts on the partnership. “The Akamai relationship puts us in a really strategic position to get more event information and intelligence from our customers who are either using the Akamai network or working with us from a DDoS perspective,” Steve said, “so the ability to join the Akamai DDoS infrastructure with our backend threat intelligence infrastructure is really a great opportunity for us moving forward.”
Akamai and Trustwave formed a strategic alliance to enhance security and protect against WAF and DDoS attacks.
Akamai’s WAF Protection and Trustwave’s SpiderLabs
So, how are Akamai and Trustwave corroborating on managed service offerings for their customers? According to Dan, Akamai had an immediate need: vulnerability testing. He explained the biased dilemma of being a WAF provider warning potential customers about a vulnerability to their application. “It’s hard for a company that has a WAF for sale to tell somebody that they have web app vulnerability,” he said. Enter Trustwave.
With this new alliance, Trustwave now serves as a credibility component, affirming customers’ need for Akamai’s WAF protection. Trustwave provides their Incident Response and Readiness services delivered by SpiderLabs, a team of over 150 ethical hackers, forensic investigators, and pretty much genius-level researchers. Their team conducts hundreds of data breach investigations annually, and offers on-call responders, resulting in an actionable testing plan for detection, triage, and containment of the breach.
Trustwave’s Global Security Report: Keeping Up with the Exponential Growth
According to the 2015 Trustwave Global Security Report, Steve explained that, “49 percent of investigations that we conducted last year were related to eCommerce web application breaches.” The median duration of a breach, from intrusion to containment, is 111 days, and in that time, “about 81 percent of victims were not able to identify the attacks themselves,” according to Steve.
From both a threat intelligence and a managed services perspective, Trustwave has heavily invested in their Big Data backend, by primarily using Hadoop technologies to build out the platform, Steve explained. “We had to make those significant investments to make sure that the scale of our operations and our intelligence capabilities are keeping up with the exponential growth of malware and security events,” he said.
With their Cloud-based TrustKeeper Portal, Trustwave customers now have “a single pane of glass for both compliance and security, with regards to PCI (Payment Card Industry) or just general security requirements,” Steve explained.
The Future for Akamai and Trustwave
In the future, Dan revealed that Akamai is exploring a more outbound approach to security services. “When you start looking at outbound (what’s coming from your origin or your hosting provider), that’s when forensics begins to become more important,” he explained. Another reason Trustwave’s team is a great addition to the Akamai solutions force.
Looking ahead, this partnership “takes our Trustwave SpiderLabs security capabilities from the Core, where we’ve had a very strong foothold today, all the way to the Cloud,” Steve said. “That’s where Akamai makes a lot of sense for us, and is really the perfect partner to help us do that.”
Akamai in Conclusion
Akamai Technologies has grown to dominate the CDN and Cloud-based security solutions sphere. By combining their 170,000-server network with the cyber security trailblazers at Trustwave, Akamai will undoubtedly serve as the uncontested leader in DDoS protection moving forward. “DDoS attacks begin and end with the ability to accept requests and bandwidth,” Dan said. The technological supremacy of Akamai and Trustwave secures the Web against DDoS attacks, risks to web applications, and the threat of precious data loss. Serving globally, the Alkamai Intelligent Platform offers uncontested security and visibility for online businesses.
To stay up-to-date and informed on the latest data recorded on the types of attacks, platforms attacks are seen on, and ports responsible for taking them in, follow Akamai’s State of the Internet Security Reports, put out quarterly.
Photo Sources: blogs.akamai.com; www.trustwave.com/home
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

