
TL; DR: NordLocker provides cutting-edge encryption for secure file storage and sharing. Its zero-knowledge architecture ensures users retain complete control over their data and privacy, whether in storage, transit, or transfer. NordLocker also makes cybersecurity simple by developing a private-by-design interface that includes drag-and-drop functionality and leveraging serverless technology for added flexibility.
If you have ever owned or rented a locker, you know the value of using one to store and protect your valuable items. A locker’s hard metallic exterior gives people peace of mind that no one will break in and steal things that should only be accessible to the owner. The user’s only job is to remember the passcode when it’s time to gather their valuables. But what if the locker’s structure is faulty? Maybe it has a broken door or a digital key that malfunctions.
In the digital world, people use file storage applications to store their data. But many don’t know that their data isn’t as secure or private as they would like it to be because of cracks or vulnerabilities in the application’s framework. As the public becomes more aware of user privacy, the demand for private-by-design resources has catapulted in the last few years because users want to keep their data secure.

NordLocker serves as a digital locker for users, providing them with file encryption software with end-to-end encrypted cloud storage and secure file sharing. The company belongs to the family of NordSecurity and offers a privacy-first solution to keep user data protected and private with zero-knowledge architecture and end-to-end encryption.
“At the forefront of digital security, zero-knowledge architecture is the most important feature that sets us apart from the competition. It is an unconditional data privacy paradigm that ensures full files’ ownership for the users, meaning only the user can access their data,” said Aivaras Vencevičius, Head of Product for NordLocker.
NordLocker ensures that users have complete control over their data and who accesses it. Its zero-knowledge technology plays a massive role in making that possible, but just as with physical lockers, password security is also essential. “In the end, this is all we ask of our users – to take simple steps to protect their digital assets by keeping their passwords secure. And leave the rest to us,” said Darius Borisas, Head of Business Development for NordLocker.
Zero Compromise With Zero-Knowledge Architecture
Users shouldn’t have to compromise their data for a convenient file storage service. NordLocker understands that and sets out to provide users with a completely secure solution. Privacy and security are the cornerstones of NordLocker’s framework, and everything the company does is based on improving those two facets.
“While other cloud solutions may prioritize features or convenience over privacy, we firmly believe that when it comes to sensitive information, there can be no shortcuts, and our zero-knowledge architecture reflects that philosophy,” said Aivaras.
The NordLocker team cares deeply about customer privacy and makes it its mission to deliver cloud solutions that stand on strict user privacy. Its zero-knowledge architecture is the most essential piece in this mission. As more users entrust their sensitive data to cloud services, they need solutions they can count on to protect their privacy.
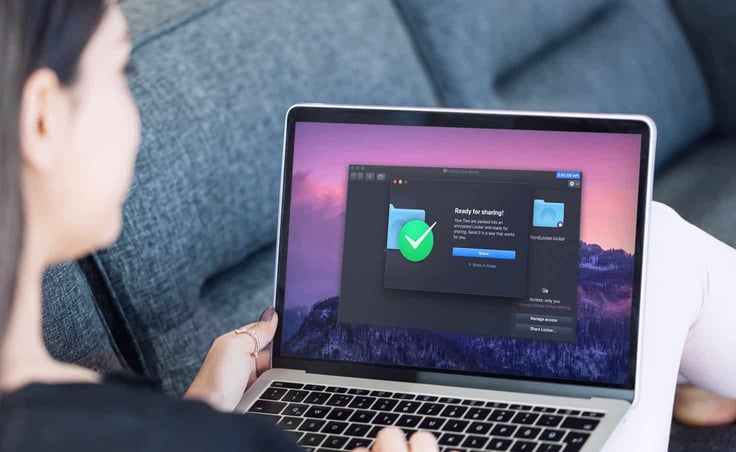
“With zero-knowledge architecture, users can rest assured that their data is always under their control and that even the service providers cannot access it. We take great pride in providing this feature to our users,” said Aivaras.
NordLocker also enlists the capabilities of end-to-end encryption to safeguard user data from unwanted eyes. The company goes a step further than other cloud providers by encrypting data not only while it is stored or in transit, but also during transfer. NordLocker encrypts the data on the user side before it reaches its software, making access impossible for anyone else.
“We don’t just carry our users’ data to a safe place – we accompany them every step of the way, opening all the doors, ensuring that only the user can access their possessions. With our end-to-end encryption technology, there is no opportunity for anyone else to access our users’ data,” said Aivaras.
Serverless and Drag-and-Drop Functionality That’s Easy to Use
Cybersecurity often comes across as complex and tricky to implement and manage. Its complexity is one of the main challenges companies face when adopting cybersecurity solutions into their operational infrastructure. NordLocker makes a conscious effort to ensure its solutions are easy to use and accessible for everyone.
“We believe security should not hinder usability, and our product strives to deliver both ease of use and security by default. Our users should not face any obstacles while using NordLocker,” said Darius.
NordLocker incorporates user-friendliness and simplicity in multiple ways. Users can sign in to all Nord products with one account for a seamless and intuitive ecosystem of safe and secure network use and digital assets. The encryption process is also simple. Users only need to enter their master password once, and all security measures will fall in place.
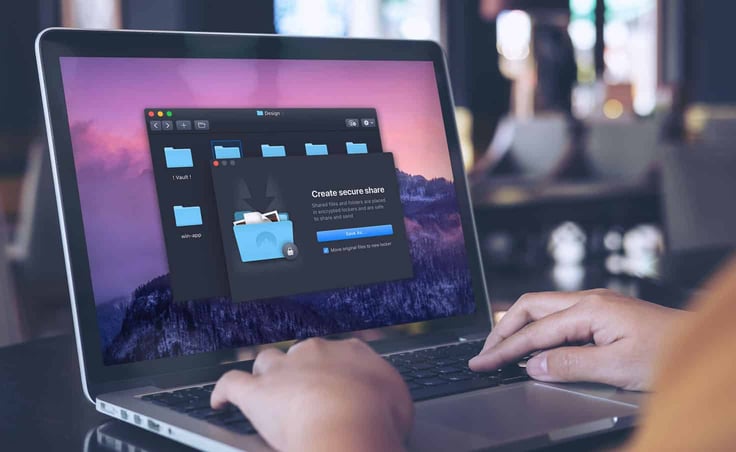
The NordLocker team has worked diligently to provide a straightforward and intuitive user interface, showing that security doesn’t have to be complicated to be performant. It does so by including drag-and-drop functionality for easier use.
“Drag and drop is an intuitive and convenient function that attempts to replicate natural user actions. Our UX design team has made it their mission to make NordLocker feel as familiar and easy to use as possible while maintaining a high-security level,” said Aivaras.
NordLocker’s serverless approach also provides top-level flexibility, giving users peace of mind about costs and performance. Eliminating the need for physical servers allows the company to leverage cloud computing and give users better scalability, cost-effectiveness, and improved performance. “By using serverless architecture, we can allocate resources more efficiently and pass cost savings onto our customers while reducing our carbon footprint,” said Aivaras.
Taking No Shortcuts to Establish Healthy Digital Hygiene
NordLocker takes no shortcuts. Darius told us the team is committed to providing the best services and doing things the right way, although it sometimes takes more time and effort. NordLocker is currently in the process of rebuilding and revamping its encryption methods. This change will also come with the release of new productivity features emphasizing collaboration.
“We plan to introduce more productivity-boosting functions while maintaining our high-security standards. Soon, businesses will be able to use NordLocker to send contracts to their vendors securely and conveniently,” said Darius.
The team plans to make NordLocker a user workspace, enhancing the experience for users with a more comprehensive platform. It will also introduce biometric-based secure access through the web so users won’t have to remember their master password to unlock their vault.
NordLocker constantly seeks out future trends in the ever-evolving cybersecurity landscape to develop its products. Its team is currently implementing a quantum encryption upgrade, which shows its drive to stay ahead of the curve.
“We take great pride in ensuring that NordLocker remains at the cutting edge of data security technology so that our customers can always trust that their information is safe with us,” said Aivaras.


