
TL; DR: By being laser-focused on providing businesses with comprehensive yet intuitive security, Check Point Software Technologies protects sensitive data and business communications from attackers while enabling users to fine-tune their security with a streamlined, unified management portal. The veteran company, established in 1993, continues to monitor the threat landscape by tracking emerging issues and encouraging enterprises to consider security vulnerabilities attached to increased mobility and virtualization. Don Meyer, Head of Marketing for Check Point’s datacenter team, identified two emerging threats to enterprise security and shared how the company’s software-driven approach bodes well for virtualization and agility.
While developing a protocol to create a unified inbox for voice and text messages in the late ’90s, Don Meyer kept running into problems — his demos wouldn’t work because of some pesky thing called a firewall.
Firewalls, which police traffic coming into and out of networks, were still rather new at the time. Check Point Software Technologies, which pioneered stateful inspection processes, was responsible for the firewall giving Don problems.
“The more I played with the product, the more I appreciated the thought that went into how well security systems could be managed,” he said. “The workflows that were utilized, even way back then, were very intuitive and business friendly.”
After roughly 15 years of interacting with Check Point security systems, Don joined the company as the Head of Marketing for the datacenter team, which seeks to protect both physical and virtual networks and help businesses securely move to cloud environments.

Don Meyer, Head of Marketing for the datacenter team, has nearly 20 years of interacting with Check Point solutions.
“With Check Point having been part of the datacenter since almost day one, with respect to security, they’re the natural partner in terms of making that transition secure and seamless for organizations,” he said. “Having dealt with the products in the past, Check Point is the furthest along in that regard. The approach Check Point takes is how they can make security work better for businesses and be an integral part of the business without having to jump through so many crazy hoops.”
Using Internal Tools and External Collaboration to Protect Users
Although malware authors use more sophisticated techniques, are better organized, and are increasingly well-funded, many of the vulnerabilities they exploit are fairly well-known, according to Don. severaThat dichotomy requires a balanced approach to security — continuing to address familiar weaknesses while staying ahead of emerging threats.
“Common exploit vectors work really well, which is why there’s such a big industry around malware and security,” he said, adding that Check Point adapts its products to safeguard those vulnerabilities. “It’s not just looking at what the new things are. It’s also maintaining what we’ve known and learned over the course of our existence and making sure that is preserved within the products as well.”
ThreatCloud: Cloud-Based Security Intelligence and Real-Time Threat Tracking
To stay ahead of attackers, Check Point relies on intelligence gathered through the ThreatCloud suite of products, which include tailored threat information feeds as well as managed security and incident response services.
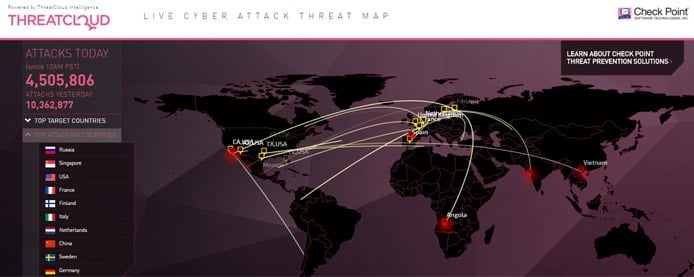
ThreatCloud gathers intelligence about vulnerabilities and displays attacks as they happen across the world.
ThreatCloud gathers information from all of Check Point’s gateways to track online attacks around the world, then displays the attacks on a live map.
“It gives us a safe place to explore these threats and figure out what they’re doing,” Don said. “Once we understand the nature of the threat, we’ll write the signatures and update every one of our gateways to now be tuned toward protecting themselves against this new, previously unknown, threat.”
Partnering With Competitors to Leverage and Share the Latest Threat Information
According to Don, security companies put aside their competing products in favor of sharing threat intelligence that benefits end users and the internet as a whole.
“If a competitor of ours finds out something that is really, really relevant to the marketplace at large, they shouldn’t hold onto that information,” he said. “That information should be public and disseminated out. The same goes for us.”
Check Point boasts partnerships with several different security organizations to stay ahead of attackers and created the Open Platform for Security, or OPSEC, integration framework. More than 350 security vendors and partners offer OPSEC-compliant products. Don also told us Check Point was recently added as a founding member of the newly formour ed Cyber Threat Alliance.
“The Alliance is a not-for-profit consortium of technology vendors and government agencies, along with nonprofit groups and corporations, with the sole goal of improving threat sharing among private and public entities,” he said.
“Our goal is to keep everyone in tune with the latest information soto we’re all armed to the teeth to try and make our customer environments as secure as we can possibly make them,” Don said.
2 Emerging Security Issues Businesses Need to Watch Out For
With the increased number of ways to store and access information, Don said security providers must exhibit the same flexibility as their customers.
“Security has to adapt and be able to accommodate these new transformations,” he said. “It gives customers a much easier time of adapting new technologies, plus gets them all the necessary tools they need to keep their environments secure. They can securely push their business forward and still maintain that agile environment they’re looking for.”
1. Malware Attacks on Mobile Devices and Other Endpoints
The Check Point team has recently noticed “an explosion” in the amount of malware targeting mobile devices, according to Don. The company addresses the vulnerability with products focused on endpoint security broadly, along with mobile security solutions in particular.

According to Don, mobile devices present the newest challenge to enterprise network security.
“The awareness, or at least the complacency, with respect to enterprise mobility is kind of surprising,” he said, theorizing the consumer-grade devices owned by employees contribute to the inaction. “However, the devices are accessing more and more data. As we digitize and cloud-enable everything, mobile devices are going to be the cornerstone to how business is conducted.”
2. Balancing Agility and Virtualization With Cloud Security
The datacenter industry is seeing a major shift from what Don called “hardware-based silos” to more agile and dynamic software-driven environments.
“This whole cloud transformation is not only really exciting, but it’s ultra-disruptive,” he said. “It’s really going to have a huge impact on how things, not only from the datacenter perspective, but how our overall organizations function as we go forward.”
The move bodes well for Check Point, according to Don, as the company started off and maintains a focus on software that can be ported into any x86-based architecture.
“We can use that to our advantage to really help organizations migrate into new places they want and still maintain the same level of security and protections they enjoy when they’re using us in other areas of the network.”
Adaptability Perks of Being a Software Company in a Hardware World
As information continues to leave physical datacenters in favor of the cloud, Don said security practices must adapt to protect the data along every step of the migration.
“The trends going forward with respect to virtualization, IoT, and whatever happens next on the enterprise front are really going to challenge everyone’s notion of what security is and what it means,” he said. “It can’t be based on hardware because there’s no more hardware; everything is floating around in the cloud.”
At the same time, Don said the company is very measured and deliberate in its approach to adopting new technologies and including them in Check Point products. The company concentrates on meeting customer needs and streamlining user experiences by tightly aligning capabilities rather than simply rushing to deploy new features that aren’t well integrated.
“At Check Point, we really don’t have that challenge,” he said. “At the same time, the technology that we do bring out is certainly world-class and fits into the moniker or modicum of us trying to deliver the best solutions we can to our customers.”
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

