
TL; DR: As security tools for virus, malware, and endpoint protection have become increasingly complex and specialized, British security company Sophos have simplified network protection with a suite of products managed from a simple, online interface. Appealing to mid-market enterprises and companies with limited resources, skills, or budgets, Sophos Central enables security teams to find threats faster, minimize their impact, and investigate how they happened. Intercept X, the newest product from Sophos, addresses the rampant threat of ransomware and other advanced threats.
Even though Sophos began producing anti-virus and encryption software in 1985, a recent push for advancement and modernization is what inspired Matt Cooke to join the British security company’s team.
“The innovation and growth occurring at Sophos were quite unique compared to some of the other security vendors that have been around for quite awhile,” he said. “Over the last couple of years, the growth and innovation have been pretty extraordinary.”
As the company was finding their foothold in the security industry in the late ’90s, Sophos added a series of data security and protection programs to their portfolio, along with remote device administration tools.
Now, the 14 network, end-user, and server security products from Sophos provide a complete — but not complex — solution to protecting devices and data that can be managed by a clean, intuitive online portal called Sophos Central. The company’s newest program, Intercept X, hit the market in September 2016 with a mission to stop ransomware, provide insights on attacks, and automatically restore your files and networks.
Why a Mix of Security Tools Run By Inexperienced Users Doesn’t Work
Security products most resonate with organizations in what Matt calls the “sweet spot” of the Sophos audience — medium-sized organizations that don’t necessarily have the resources, skills, or budgets to build out a large security team.
“They don’t want to have the complexity of plugging security together from different vendors,” he said. “They want security to operate more as a simple system where their components automatically talk to each other and can help give them the kind of best-in-class protection that they need.”
Problem #1: Not Sure How to Secure Networks
With so many options and programs on the market, small- to medium-sized organizations are frequently overwhelmed and unsure when it comes to choosing and implementing security tools, according to Matt.
“Half of the time, it’s just knowing the best thing to do,” he said. “Piecing all that together can be quite complex.”
Organizations might wonder if they need to deploy endpoint protection, which anti-virus solution to use, and if they should learn about server protection or anti-exploit options.
“It ends up costing a lot more, certainly from a support or administration perspective, but it also makes it much harder to see where their vulnerabilities exist,” Matt said of seeking solutions from multiple vendors.
Problem #2: More Vendors Often Mean More Headaches
Organizations that use security programs from multiple vendors might think they’re “spreading their bets,” as Matt calls it, by not relying on the same intelligence or not being susceptible to the same weaknesses.
“An element of that is true, but the downside is that you lose the contextual sharing or decision-making based on exactly what’s going on,” he said, alluding to a scenario where an anti-virus program might alert the firewall about an infected network device. “Organizations can end up in a situation where they’ve deployed all these individual products to try and give them better security, but what it actually ends up doing is causing them more headaches. It’s sharing that contextual information that gives us the edge and adds value to using one vendor for multiple services.”
How Sophos Products are the Solution for Simple, Synchronized Security
Sophos encourages the sole-security-vendor approach with Sophos Central, an online hub that lets customers interact with all their security programs in a cloud-based portal. For the users who prefer multiple vendors, however, Intercept X provides an added layer of protection from exploits and ransomware.
“We try to allow them to get the best of both worlds,” Matt said. “Our focus is complete security, making it simple, and still having that granular control underneath.”
Sophos Central: Unified Console for Managing Multiple Products
By seamlessly managing multiple users, devices, and Sophos products, the Sophos Central interface synchronizes security by delivering simple, complete security through the Cloud.
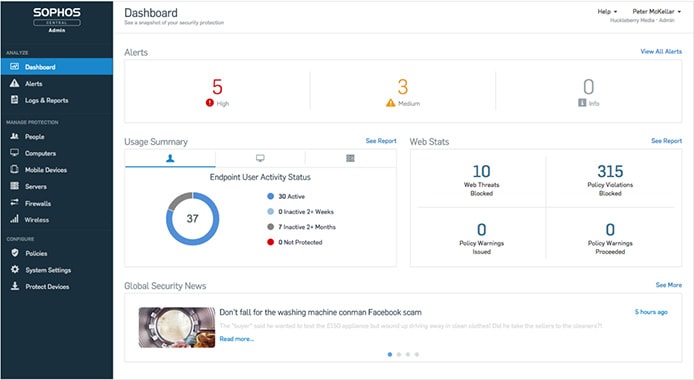
Sophos Central’s intuitive dashboard allows customers to quickly navigate among multiple security products.
“It’s the single place where a customer can go to configure the security policies that apply to the user,” he said.
With multiple products on Sophos Central, Matt said programs would work together to isolate an impacted machine before it can do more damage across a customer’s network.
“The centralized platform actually facilitates that,” he said. “That allows us to start having individual security products sharing telemetry information to make decisions that make the customers’ lives a lot better.”
Once a threat is remediated, Sophos Central provides a visualization of what occurred — where did it start and what files were affected?
“We can show the administrators the files it downloaded and accessed,” Matt said. “That allows us to then automatically clean everything out because we know everything that happened. As well as just removing the malware, we can actually undo the things it did.”
Intercept X: New Approach to Protecting Endpoints From Exploits
With the new anti-exploit and anti-ransomware program Intercept X, Matt said that Sophos is tackling next-generations threats.
Ransomware, which encrypts a user’s files and holds them hostage until a ransom is paid, massively disrupts business productivity.
Intercept X includes CryptoGuard, which Matt said is a very effective way of monitoring disc and file activity to see if files are unexpectedly being encrypted.
“When we see that process taking place, we can immediately stop that threat from happening and actually roll back any changes,” he said. “From an end-user’s perspective, that’s kind of ideal. You get ransomware and almost nothing happens. You get a little popup to tell you, but it actually has no impact.”
Sophos Crosshairs in 2017: Ransomware and Malicious Data Encryption
For too long, ransomware challenged security companies and impacted their customers by infiltrating many endpoint protection and anti-virus programs.
“It can use different delivery methods than what people are used to seeing with traditional viruses and malwares,” Matt said, explaining that ransomware often targets software vulnerabilities to make an application “behave in ways it shouldn’t” to deliver malicious code to the device.
The Sophos team has identified the most common methods malware creators use and installed systems and protections to prevent them, according to Matt. “This will actually stop a lot of the malware getting down onto the machine in the first place,” he said.
The Vibrant Atmosphere and Quick Pace of Innovation at Sophos
Since joining the Sophos team at their Abingdon, England, headquarters a year ago, Matt has continued to marvel at the hyperactive energy and passion among his coworkers.
“One of the fantastic things I found was that immediately I was coming into an organization where you can make stuff happen pretty quickly,” he said. “If you’re coming up with good ideas and socializing those ideas with people, you find they get turned around and actually make a really big difference for our customers. That’s really what we’re all trying to do: make our customers’ lives as easy as we can and protect them the best way possible.”
HostingAdvice.com is a free online resource that offers valuable content and comparison services to users. To keep this resource 100% free, we receive compensation from many of the offers listed on the site. Along with key review factors, this compensation may impact how and where products appear across the site (including, for example, the order in which they appear). HostingAdvice.com does not include the entire universe of available offers. Editorial opinions expressed on the site are strictly our own and are not provided, endorsed, or approved by advertisers.
Our site is committed to publishing independent, accurate content guided by strict editorial guidelines. Before articles and reviews are published on our site, they undergo a thorough review process performed by a team of independent editors and subject-matter experts to ensure the content’s accuracy, timeliness, and impartiality. Our editorial team is separate and independent of our site’s advertisers, and the opinions they express on our site are their own. To read more about our team members and their editorial backgrounds, please visit our site’s About page.

